Security Policy, version 1.0 January 31, 2008
HP StorageWorks Secure Key Manager
Page 13 of 26
© 2008 Hewlett-Packard Company
This document may be freely reproduced in its original entirety.
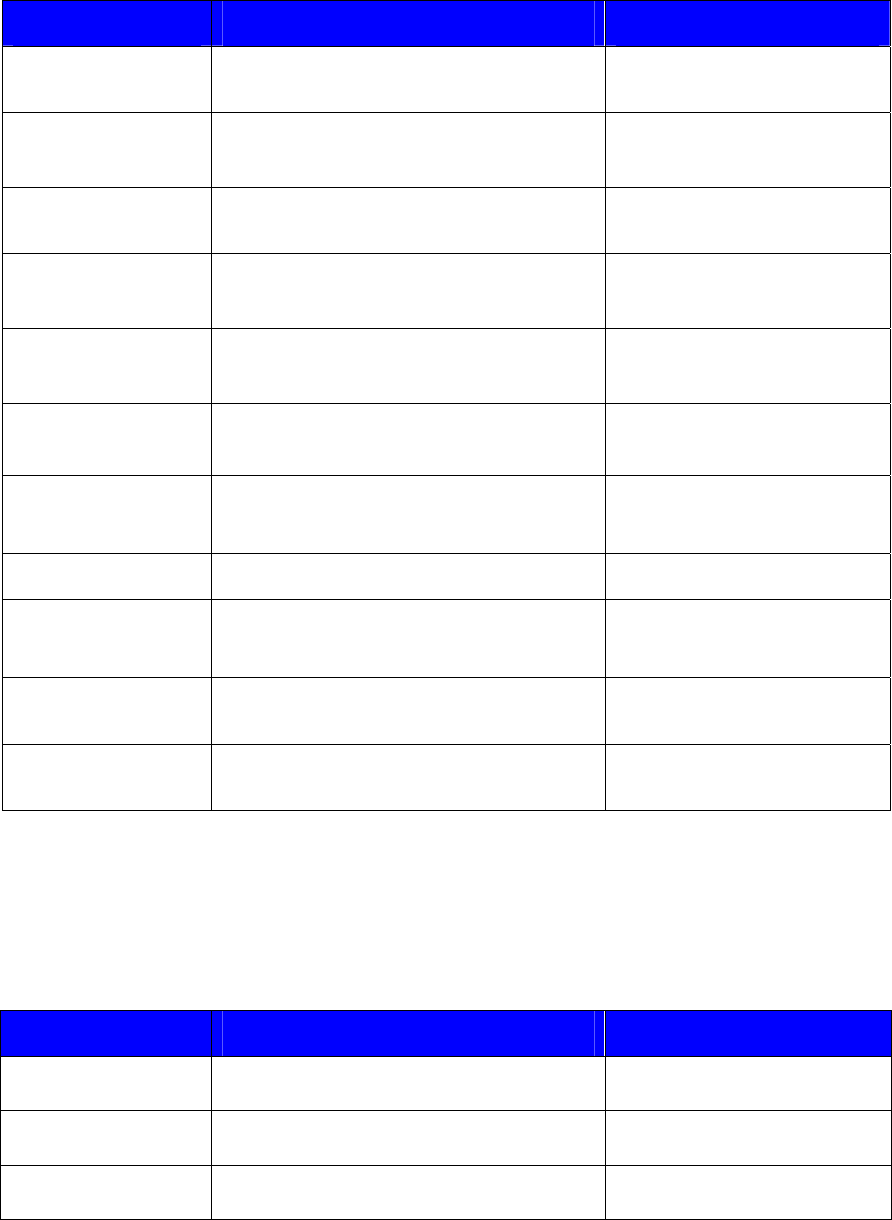
Table 7 – User Services
Service Description Keys/CSPs
Authenticate to SKM Authenticate to SKM with a username and the
associated password
User passwords – read
Generate key Generate a cryptographic key
Client keys – write
;
PKEK – write.
Modify key meta data Change the key owner or update/add/delete
the custom attributes
None
Delete key Delete a cryptographic key
Client keys – delete
;
PKEK – delete.
Query key meta data Output key names and meta data that the
User is allowed to access
Client keys – read
;
PKEK – read.
Import key Import key Client keys – write;
PKEK – write.
Export key Export a cryptographic key Client keys – read;
PKEK – read.
Export Certificate Export a certificate Client certificate – read
Clone Key Clone an existing key under a different key
name
Client keys – write, read;
PKEK – write, read.
Generate random
number
Generate a random number ANSI X9.31 DRNG seed – write,
read, delete
Manage operators Only users with administration permission can
create, modify, or delete module operators
User passwords – write, delete
2.4.3 HP User Role
The HP User role can reset the module to an uninitialized state in the event that all Crypto Officer passwords are
lost, or when a self-test permanently fails. See Table 8 – HP User Services. The keys and CSPs in the rightmost
column correspond to the keys and CSPs introduced in Section 2.7.1.
Table 8 – HP User Services
Service Description Keys/CSPs
Authenticate to the
module
Authenticate to SKM with a signed token HP User RSA public key – read
Reset factory settings Rollback to the default firmware shipped with
the module
All keys/CSPs – delete
Restore default
configuration
Delete the current configuration file and
restores the default configuration settings
None
